-
Impulses
- Impulses overview
-
Transformer manufacturers
- South America's champions of the energy transition
- Traction Transformers – Future on the Rail
- Time of the giants: XXL transformers for more power
- "Reinhausen is ready to deliver!"
- Oversized de-energized tap-changers
- The most powerful transformers in the world for a 1,100 kV HVDC line in China
- "We are in a growth market with the VRDT"
- Digitalization turnaround: GANZ Intelligent Solutions relies on cooperation with MR
- "Transitioning to a solution provider presents a major opportunity for transformer manufacturers – and digitalization can help!"
-
Digitalization
- How AI can lend a hand
- myReinhausen: MR's central digital customer platform
- Why data centers (may) never fail
- Automation? (Cyber-) Secure!
- Globally unique: MESSKO® MTRAB® dehydrating breather communicates via cell phone app
- Remote Solutions: Professional help from a distance
- "Digitalization of the power grids will only work with comprehensive security measures"
- Why are you digitizing your transformers? Three questions for Rúnar Svavar Svavarsson.
- Six challenges, six solutions – Intelligent sensors for safe transformers
-
Energy transition
- The VRDT is the ideal solution to solve voltage problems in our distribution grids
- Making transformers more sustainable
- 940 tons of power regulation
- Sunny prospects: Municipal solar storage devices
- Four reasons why regulated distribution grids are the future
- "The energy transition is taking place in the distribution grids"
- Five theses on the future of power grids
- Storage at all network levels
- Test systems for the energy revolution
- Climate change, energy revolution and the future of power grids?
- A new design for utility poles
-
Wind and solar power
- The North Sea as Europe's green power plant
- Sahara electricity - safe for the island
- Are wind farms the new power plants?
- Direct current at all grid levels
- The MSCDN plant – the new "power plant generator" for stable grids
- Clean power grid with high-frequency filters
- Weatherproof cable testing for offshore wind parks
- VRDTs for Australia's distribution grids
- Lifetime optimization
- Power supply in industry
- Globalization
- Impulses overview
-
Transformer manufacturers
- South America's champions of the energy transition
- Traction Transformers – Future on the Rail
- Time of the giants: XXL transformers for more power
- "Reinhausen is ready to deliver!"
- Oversized de-energized tap-changers
- The most powerful transformers in the world for a 1,100 kV HVDC line in China
- "We are in a growth market with the VRDT"
- Digitalization turnaround: GANZ Intelligent Solutions relies on cooperation with MR
- "Transitioning to a solution provider presents a major opportunity for transformer manufacturers – and digitalization can help!"
-
Digitalization
- How AI can lend a hand
- myReinhausen: MR's central digital customer platform
- Why data centers (may) never fail
- Automation? (Cyber-) Secure!
- Globally unique: MESSKO® MTRAB® dehydrating breather communicates via cell phone app
- Remote Solutions: Professional help from a distance
- "Digitalization of the power grids will only work with comprehensive security measures"
- Why are you digitizing your transformers? Three questions for Rúnar Svavar Svavarsson.
- Six challenges, six solutions – Intelligent sensors for safe transformers
-
Energy transition
- The VRDT is the ideal solution to solve voltage problems in our distribution grids
- Making transformers more sustainable
- 940 tons of power regulation
- Sunny prospects: Municipal solar storage devices
- Four reasons why regulated distribution grids are the future
- "The energy transition is taking place in the distribution grids"
- Five theses on the future of power grids
- Storage at all network levels
- Test systems for the energy revolution
- Climate change, energy revolution and the future of power grids?
- A new design for utility poles
-
Wind and solar power
- The North Sea as Europe's green power plant
- Sahara electricity - safe for the island
- Are wind farms the new power plants?
- Direct current at all grid levels
- The MSCDN plant – the new "power plant generator" for stable grids
- Clean power grid with high-frequency filters
- Weatherproof cable testing for offshore wind parks
- VRDTs for Australia's distribution grids
-
Lifetime optimization
-
Power supply in industry
-
Globalization
Impulses - Portfolio
-
Career
Career
-
Company
Company
Transformer Automation
CONTROL. REGULATE. MONITOR.
The growing number and greater average age of power transformers, and increasingly more demanding technical requirements on monitoring, control and regulation, are presenting growing challenges for the work of asset managers and grid management.
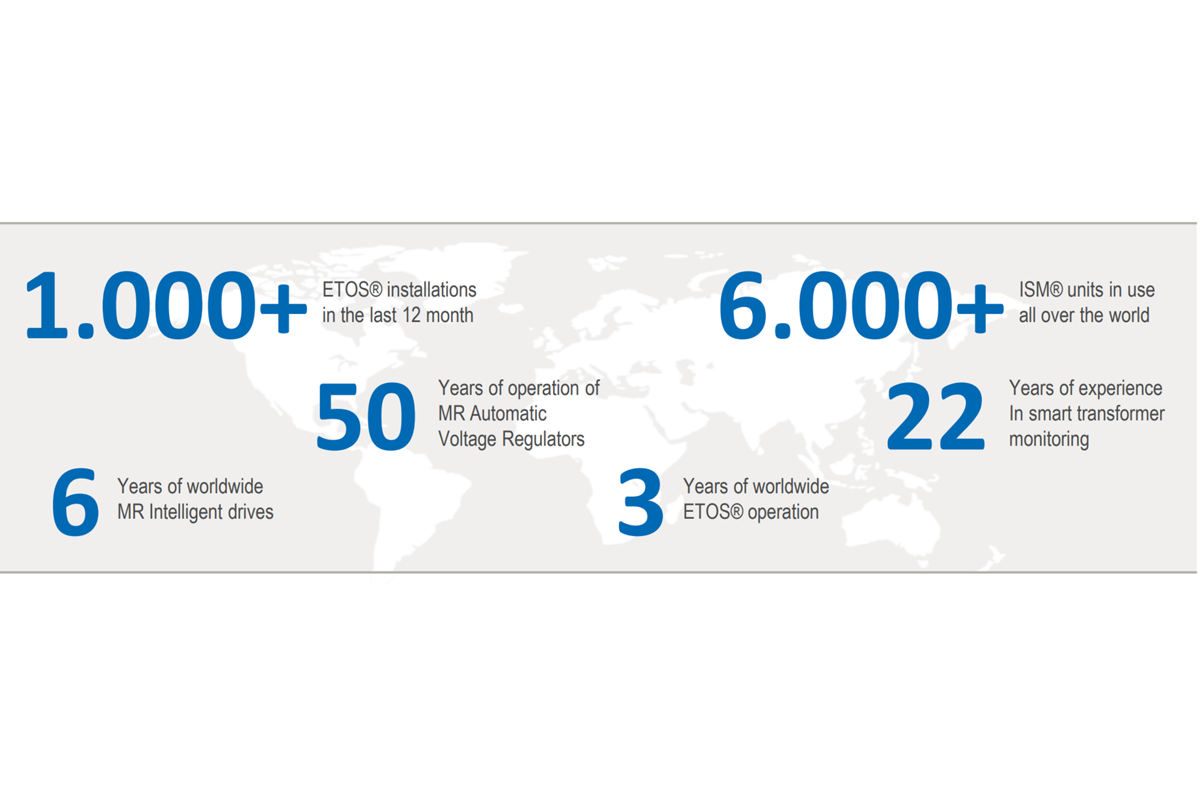
MR has over 20+ years of experience in automation and digitalization of transformers and gained valuable lessons from tens of thousands of projects around the world and listening to our customers helped us in prioritizing and making strategic portfolio decisions of our continuous ETOS® developments. At MR we believe in the value of standardization, of system integration and of transformer intelligence to increase reliability, to detect incipient faults, to assist with issue resolution and to increase flexibility and maximize the intake of renewable energy sources.
Intelligent and modular.
Intelligent and modular.
Our solution for the automation of power transformers is called ETOS® (Embedded Transformer Operating System) and is the world's first open operating system for intelligent transformers.
We offer a manufacturer-independent system for monitoring, controlling and regulating power transformers. Depending on the customer's requirements, the desired range of functions can be implemented on a modular basis - for different types, power classes and areas of transformer application.
ETOS® can be easily integrated or retrofitted in any environment. On one transformer or an entire fleet.
And best of all: This added value is absolutely system cost-neutral for you!
ETOS® – Modular function packages
| ETOS® | ETOS® TD | ETOS® ED | |
| Drive OLTC | x (Top Drive) | x (Side Drive) | |
| Transformer Monitoring | o | o | o |
| OLTC Monitoring | x | x | x |
| Bushing Monitoring | o | o | o |
| DGA Monitoring | o | o | o |
| Voltage Regulation | o | o | o |
| Cooling Control | o | o | o |
| x: standard o: optional |
ETOS®
ETOS® ED
ETOS® TD
MCONTROL®

We are here for you. Wherever you are.
Looking for the right contact partner?
Do you have a concern, but don't know whom you should contact? You will find that information in our contact overview. In the event of any technical disturbances, our 24/7 support is always at your disposal.
Welcome to myReinhausen
myReinhausen is MR's central, digital customer platform. On myReinhausen, customers can access customer-specific MR information as well as numerous free features related to the MR portfolio.
myReinhausenJoin Reinhausen family
Find your ideal job quickly!
Check our vacancies here. Apply today and contribute at the world market leader in energy technology keeping the energy supply stable in the future.